Torrentflux-b4rt started out as an attempt to integrate all the existing torrentflux hacks that users have made over the years. As they explain on their website: Free and open-source software portal. One of the key targets for future releases was the separation of the front-end from the back-end. Unlike most BitTorrent clients , its main user interface is a web interface. Please help improve this article by introducing citations to additional sources. 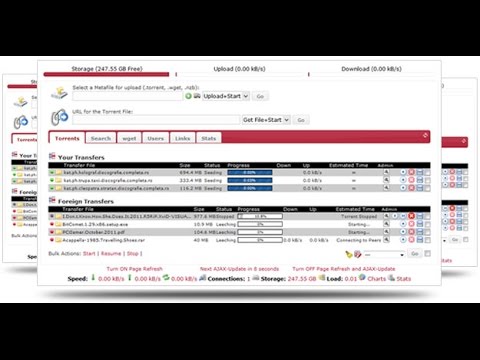
| Uploader: | Fenrishicage |
| Date Added: | 8 November 2009 |
| File Size: | 24.54 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 75158 |
| Price: | Free* [*Free Regsitration Required] |
Unlike most BitTorrent clientsits main user interface is a web interface. Numerous "hacks" have been written to add additional functionality.
TorrentFlux-b4rt incorporates many of the mods created by the community, as well as torrentfflux new features and display themes, into a single package. The main user interface is accessed via a web browser and it widely used by members of private BitTorrent trackers.
The latest Windows version is 1. While that might not initially sound that threatening, for private tracker users it constitutes quite a security breach.
Facebook Takes Down TorrentFreak Post Over ‘Infringing’ Meme
The software runs on any Unix like OS. TorrentFlux-b4rt is a popular spin-off of TorrentFlux, an open source web based system for managing BitTorrent downloads on seedboxes.
Getting access to this allows the attacker to masquerade as the other user on private trackers. List List of P2P protocols. Torrentflux-b4rt started out as an attempt to integrate all the existing torrentflux hacks that users have made over the years. Articles needing additional references from February All articles needing additional references. In addition it can handle. List of P2P protocols. This article relies largely or entirely on a single source. Torrentflux-b4rt is pretty much a fully-featured filesharing portal, it comes with a built in file-manager that can extract rar-archives, and a great web-player VLC that allows you to stream media files to your local computer.
Retrieved from " https: Please help improve this article by introducing citations to additional sources. It has a command line version for advanced users, so you can set cron jobs to watch folders for new torrent files, automatically download. It is an ideal solution if you want to manage your downloads on a computer other than your desktop machine.
The most recent beta release also includes support for ADOdballowing for use of other database backends. However, the modifications implemented in b4rt make it much more than a BitTorrent client. A member of support staff at Xirvika company selling seedboxes and other related services, told us a little about b4rt and the serious exploit one of their customers has just discovered. The reason for this is that project development for TorrentFlux-b4rt has come to an end, the continuous stream of spam on the forums, a website that had not been updated for years and a lack of permissions and access for others to update the project and the site.
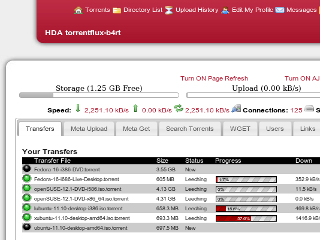
The newer versions of TorrentFlux-b4rt are completely rewritten, and no longer based on the original TorrentFlux source code. Its web interface allows it to be operated on a remote server, which is useful for file services based at an Internet service center.
The software currently includes 4 different BitTorrent clients, Azureus, Transmission, BitTorrent mainline and BitTornado, which can be configured separately for every. You can either pimp an old and unused desktop PC, or install it on a remote server.
The latest release is 2. From Wikipedia, the free encyclopedia. The software is easy to install and configure through any web browser. Relevant discussion may be found on the talk page.
Download from BitTorrent and Usenet with Your Web Server - TorrentFreak
Free and open-source software portal. B4tr of the key targets for future releases was the separation of the front-end from the back-end. This enables the attacker to obtain another user's unique passkey and masquerade as them on private trackers.

Комментарии
Отправить комментарий